NR583NP Week 7 Discussion Cybersecurity
Class: NR583NP Informatics for Advanced Nursing Practice
Preparing the Discussion
Follow these guidelines when completing each component of the discussion. Contact your course faculty if you have questions.
General Instructions
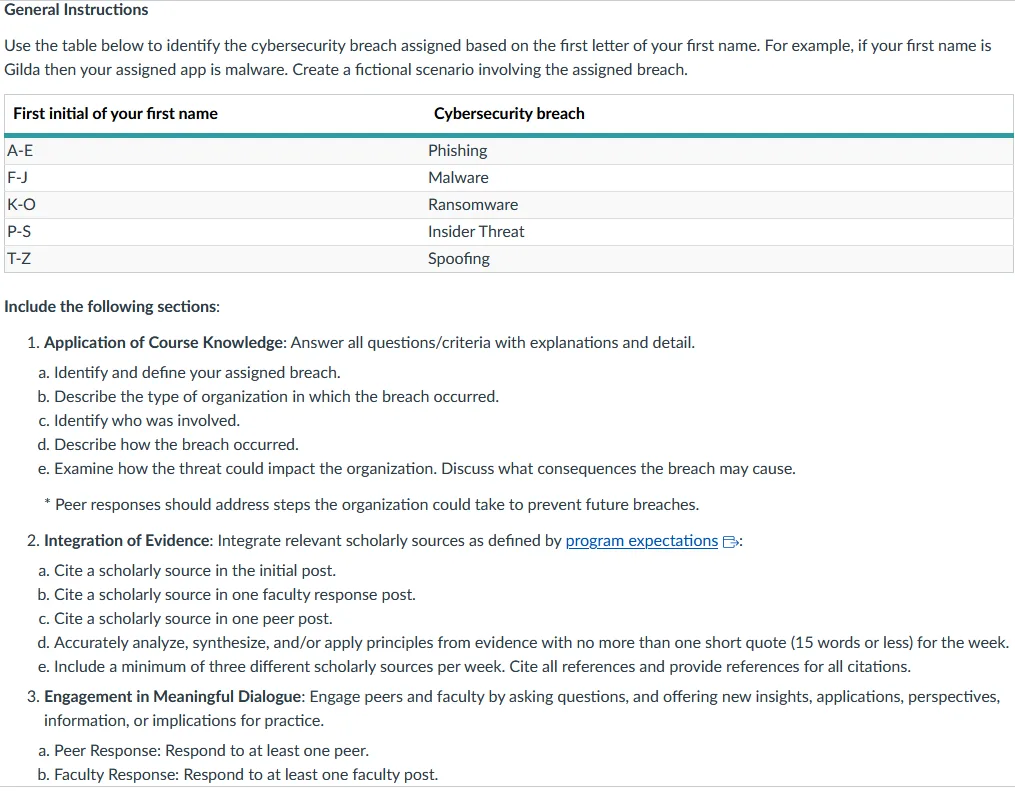
Use the table below to identify the cybersecurity breach assigned based on the first letter of your first name. For example, if your first name is Gilda then your assigned app is malware. Create a fictional scenario involving the assigned breach.
| First initial of your first name | Cybersecurity breach |
| A-E | Phishing |
| F-J | Malware |
| K-O | Ransomware |
| P-S | Insider Threat |
| T-Z | Spoofing |
Include the following sections:
- Application of Course Knowledge: Answer all questions/criteria with explanations and detail.
-
- Identify and define your assigned breach.
- Describe the type of organization in which the breach occurred.
- Identify who was involved.
- Describe how the breach occurred.
- Examine how the threat could impact the organization. Discuss what consequences the breach may cause.
* Peer responses should address steps the organization could take to prevent future breaches.
- Integration of Evidence: Integrate relevant scholarly sources as defined by program expectations
-
- Cite a scholarly source in the initial post.
Solution
Phishing is a type of cybersecurity breach in which attackers attempt to deceive individuals into providing sensitive information, such as login credentials, financial details, or personal data, by posing as a trustworthy entity. This is typically……………………Get this solution for $5.00


Reviews
There are no reviews yet.